Security is important, but it is also an uncomfortable topic, because it can’t be covered by one tool alone, and it’s also not easy to put a price tag on it. Usually, security measures mean extra effort instead of easy access. In daily life, this could be additional locks on doors and windows and more keys to schlep around. But the best locks are useless when you leave the balcony door open, either by accident or to get in more easily yourself. And if you have friendly thieves knocking on your door for a cup of tea, the locks won’t help you either.
If you are the homeowner, it’s on you to secure your property. But what if you are a tenant? What’s your responsibility, and which parts are on your landlord? And what about a hotel room or a holiday apartment while on vacation? Similar considerations apply when reflecting on IT security on-premises and in the cloud.
When choosing a new cloud provider, there are a lot of things you have to take into account. If you are already using cloud services, adding new tools (additional cloud services, or software like Dataiku) to the infrastructure of the same cloud provider will usually be more straightforward than combining services from different cloud providers. But depending on the type of cloud service, the customer and the cloud provider have ownership of different responsibilities. In this blog, we will give a high-level overview of IT security, as well as explain what you can expect from a cloud provider, key considerations, and concrete steps to take when choosing one.
IT Security in General
The aim of IT security is to guard systems and data against unwanted access, irrespective of their location (your own data center or some other location, like an internet host or in a public cloud). Such unwanted access can lead to theft of intellectual property, loss of service continuity, or the collection of competitive intelligence and your competitive edge. This includes targeted attacks from external or internal culprits, as well as unintended mishaps by employees. Data mustn’t be deleted, altered, copied, or even read by entities that aren’t authorized to do so. Systems are supposed to be performant and run without interruptions — and they certainly shouldn’t provide a backdoor for attacks. IT security ensures undisturbed services and prevents system outages and their resulting costs.
First and foremost, security breaches have to be avoided. Some form of monitoring should record that there really were no incidents. But if a security breach happened, timely notifications are key to limiting the damage. Traceability of the who and when of the theft, copying, deletion, or modification of what exactly is crucial, and also necessary for potential claims for damages.
An overview of the plethora of topics that play a role in IT security are shown in Figure 1. Depending on the industry, different parts of a company’s or government agency’s security strategy might be subject to regulations.
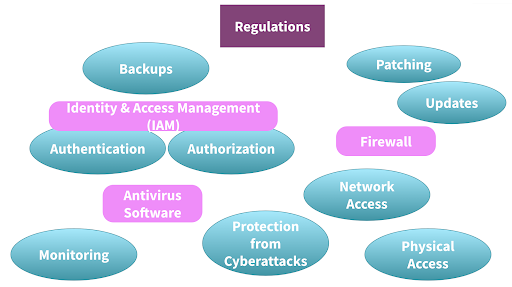 Figure 1: Crucial parts of an IT security strategy — their scope might be subject to regulations
Figure 1: Crucial parts of an IT security strategy — their scope might be subject to regulations
Even if a breach like malware is discovered early, i.e., before it was able to do it’s intended malicious work, it always leads to outages: recovery efforts include clearing any remains of the breach, such as fixing security flaws before systems are fully usable again.
An example is the incident at German Justus-Liebig-Universität Gießen on Dec. 8, 2019 (full details can be found here). The university statement read, “After a serious IT security problem, Justus Liebig University Giessen has shut down its servers for security reasons. The university has been offline since Sunday afternoon; internet, email systems and internal networks are not in use. JLU is pressing charges on suspicion of a cyber attack. Currently, it is not possible to state the exact cause of the IT problems, also on account of the ongoing inquiry.”
More than a month later, the IT infrastructure was still not fully restored, despite the immediate shutdown of all servers directly after discovery of the attack. The new statement from JLU President Prof. Dr. Joybrato Mukherjee read, “Almost five weeks after the criminal cyber attack of 8 December 2019, Justus Liebig University Giessen (JLU) is approaching several milestones on their way to full functionality of their digital systems. We hope that by mid-February — and thus still during the current lecture period — we will be out of the woods.”
Cloud Services
Cloud services are a different solution than internet hosting. The common acknowledged definition is the NIST definition of cloud computing:
“Cloud computing is a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction.”
In general, cloud services are grouped into three categories:
- IaaS (Infrastructure-as-a-Service) provides the infrastructure for installing software like operating systems or applications. This infrastructure includes storage, processors, and networks. The customer has access to the operating system, storage, installed applications, and certain network components like firewalls.
- PaaS (Platform-as-a-Service) provides the infrastructure, including operating server, system, storage, network etc. for installing and maintaining applications. The customer doesn’t have any control over the underlying cloud infrastructure.
- SaaS (Software-as-a-Service) provides applications as cloud services. The customer cannot access the underlying infrastructure, but might have restricted access to user specific configurations of the application.
There are several advantages of using cloud services over on-premises data centers: scalability with the possibility of pay-as-you-go billing, redundancy, high availability, shifting from capital expenditures (CAPEX) to operating expenses (OPEX), standardized software, access to the latest hardware like GPUs, and a reduced dependency on finding experts for the in-house maintenance of systems.
Cloud providers are generally really stringent with the measures for safeguarding their data centers — most of the time even more than it would be enforced in on-premises data centers. This is the reason that hybrid architectures that contain on-premises IT infrastructure as well as cloud services (from one or more cloud providers) are becoming more and more popular.
Depending on the type of cloud service, the customer and the cloud provider have ownership of different responsibilities and courses of action. An example is the storage of personal data in different types of cloud services:
- IaaS: The customer installs all applications themselves. The cloud provider cannot know if personal information is stored and processed in this cloud service. All capacity to act as well as all responsibility for handling personal data according to the General Data Protection Regulation (GDPR) is with the customer.
- SaaS: If the provided software is intended to work with personal data, the cloud service should provide corresponding security functionality, like encryption and fine-grained access control.
Minimizing Risks in Cloud Environments
How to deal with the fact that the responsibility and liability is still on the customer’s side, but the possible course of action might be handed over to the cloud provider when using cloud services? We will give some guidance for the most pressing points. For a detailed list of the important topics during evaluation and security management of cloud environments we recommend the two white papers “Cloud Security Standards: What to Expect & What to Negotiate” and “Security for Cloud Computing Ten Steps to Ensure Success.”
Processes for Governance, Risk Assessment, and Compliance
Details for the processing of data are defined in a legally binding Data Processing Agreement (DPA). This includes type, duration, and causes for data processing, the type of (personal) data, and rights and obligations of the cloud provider as well as of the customer. Generally, DPAs are an essential part of being compliant with regulatory requirements like:
- General Data Protection Regulation (GDPR)
- California Consumer Privacy Act (CCPA)
- Health Insurance Portability and Accountability Act (HIPAA)
- Family Educational Rights and Privacy Act (FERPA)
- Payment Card Industry Data Security Standard (PCI DSS)
Further important factors are certifications and standards. Be aware that cloud services might be certified, but the cloud providers themselves usually are not. Also, these certifications are the result of an auditing process at a certain point in time. Important standards are the ISO/IEC 27000-series (in particular 27017 and 27018), ISO/IEC 19086, ISO/IEC 27036-4, and ISO/IEC 2000. These standards apply to different aspects of cloud security, like the protection of personal data and risk management.
Auditing
What constraints for auditing do you have, and can the cloud provider support these? Is self-auditing sufficient, or should a third party audit the cloud provider? Details should be written down in the Cloud Service Agreement (CSA, see below).
So-called Cloud Access Security Brokers (CASB) can be really useful for monitoring all activity between users and cloud services and enforcing security policies. But it is necessary to have a close look at their respective capabilities, because CASBs are not standardized yet.
Management of Users, Roles, and Identities
Managing users, roles, and identities has two facets: first, from the cloud provider’s side regarding their customers, and, second, from the customer’s side for their own staff. Access to a customer’s data and applications from the cloud provider’s side has to be regulated individually for every cloud service. A common standard that should be utilized is multi-factor authorization. Additionally, all access requests have to be logged. The customer must be able to define fine-grained access rights and roles for every one of their cloud services, following their own security policies.
Protection of Data Privacy
Hybrid and multi-cloud architectures pose particular challenges regarding data protection. Data encryption is important for both data-at-rest and data-in-motion. Encryption keys should be stored by the customer. This minimizes the risk for data loss, alteration of the data, and unauthorized access.
Protection of personal data became a central issue with regulations like the General Data Protection Regulation (GDPR). Access control and data masking are crucial topics to ensure compliance with these regulations. Depending on the type of cloud service (IaaS, PaaS, SaaS, see above), the cloud provider can or has to provide suitable tools. But in the end, the protection of data privacy is the responsibility of the user of the cloud services.
Network and Network Connections
Security measures have to include the cloud service itself, but also all network connections. The data has to flow uninterruptedly, but malicious traffic has to be blocked. Usually, the cloud provider cannot distinguish between legitimate and non-desirable data traffic in their customer’s services. Besides the basic protection of the network perimeter (e.g., against denial-of-service attacks or traffic to malware ports) the cloud provider should also provide tools that enable the customer to protect their environments. This includes monitoring and access to log files, as well as a timely notification in case of a security incident.
Cloud Service Agreement (CSA) and Service Level Agreements (SLAs)
Responsibilities of both the customer and the cloud provider are defined in the Cloud Service Agreement (CSA). This includes certifications, implemented standards, reporting of incidents, recovery after outages, and metrics. Part of the CSAs are the Service Level Agreements (SLAs). These specify clear expectations about performance issues and frequency and type of possible outages of the cloud services.
Exit Process: ‘The Right to be Forgotten’
What happens if you want to switch cloud providers in the future, or if you want to bring functionality back into your own data center? A possible exit process should be defined before a contract is signed. This includes the guaranteed deletion of backups, logs, etc. after a defined timespan after a migration, but also the right to delete all data completely. Besides costs for the upload of data to a cloud service (inbound traffic), the costs for getting the data out of the cloud service (outbound traffic) should also be taken into account. Costs for outbound traffic can vary between cloud providers.
Differences Between Cloud Providers
Different cloud providers offer different cloud services, but these are subject to change depending on different factors. When choosing a cloud provider you should always take into account the following topics:
- Which security features are built into the cloud services, and what can you get as an extra service (possibly with extra costs)? Are there security aspects that aren’t covered (or cannot be covered) by the cloud provider?
- Depending on the cloud provider, defaults for open ports and permitted protocols can be different. After provisioning, all ports may be closed, and the ones needed have to be opened specifically. But also the opposite can be true, and it’s on the customer (you!) to remediate this in order to eliminate security risks.
- How fast are the activity logs updated — are new entries visible in seconds, minutes, or even hours? Where and how can you access these logs?
Concrete Next Steps for Choosing a Cloud Provider
Where to start when choosing a cloud provider? What considerations are important? Ask yourself the following questions.
1. What do you need exactly?
What functionality should a certain cloud service provide to cover the technical needs in a project? To which regulations and policies do you (and therefore also the cloud provider) have to comply? Which accounting approach would be optimal? What IT infrastructure already present has to be integrated?
2. Who is responsible for what?
Responsibilities are written down in the Cloud Service Agreement (CSA) as well as in the Service Level Agreements (SLAs). You should search for possible gaps in the coverage of important topics: Are there aspects that aren’t covered in the agreements, but that can’t be fulfilled by the customer themselves because of technical reasons?
3. What security standards are implemented?
Security standards guarantee the use of best practices — internally as well as on the cloud provider’s side. They also ensure integration with existing infrastructure. They also help to maintain flexibility by avoiding vendor lock-in. Furthermore, security standards facilitate the compliance with regulations and policies.
4. Which experts should be consulted for a decision?
Usually the involvement of the IT department, Chief Security Officer (CSO) and the legal department is necessary. But often there are other departments, like procurement, that have to be included, too.
5. All open questions should be clarified before signing a contract!
What if you already chose a cloud provider for a previous project, and you now want to add new software or cloud services? For example, Dataiku will securely connect to your already existing infrastructure like storage and compute, but it will also leverage existing security measures for authentication and authorization. This is independent of the location of the installation (cloud or on-premise). A detailed audit trail as well as integration with your monitoring tools helps you to reduce complexity while providing full transparency.
Looking Ahead
As usual, the first thing to do is to define your objectives clearly. Based on these goals, a fast and effective implementation can be planned. Try to include all parties into the decision making process that will later be involved in resulting projects — for implementation as well as maintenance. And don’t forget: The most frequent reason for issues is human error. You should plan for proper education and training for all users.




